SHA256 Hash Generator: Create Secure SHA-256 Hashes Online Instantly
Our SHA256 hash generator provides a quick and efficient way to generate SHA256 hashes online, offering a powerful solution for encrypting and securing your data. Whether you’re a developer working on password hashing or a cryptocurrency enthusiast involved in blockchain technology, SHA256 is a trusted and widely-used algorithm. Learn more about what SHA256 is and why it’s essential for secure encryption.
What is SHA256?
SHA256, or Secure Hash Algorithm 256-bit, is part of the SHA-2 family of cryptographic hash functions developed by the National Security Agency (NSA). It is a one-way hash function that converts any input data into a fixed-length, 256-bit hash value, regardless of the input size. The SHA256 algorithm is widely used because it provides a higher level of security compared to older hash algorithms like MD5 and SHA1.
SHA256 is a critical component in many applications, including password hashing, file verification, and blockchain technologies. Its strength lies in its resistance to collision attacks, making it a popular choice for modern cryptographic needs.
Common Uses of SHA256 Hashing
1. Password Hashing
SHA256 is commonly used in password hashing to store user credentials securely. Instead of storing plaintext passwords, systems convert them into SHA256 hash values, which are then stored in databases. This ensures that even if the database is compromised, attackers cannot easily reverse the hash back into the original password.
Many systems also use salts in combination with SHA256 to further protect passwords from brute-force attacks and rainbow table exploits. Due to its cryptographic strength, SHA256 is preferred over weaker algorithms like MD5 and SHA1 for password security.
2. Data Integrity and Verification
One of the main applications of SHA256 is verifying the integrity of files and data. When downloading software or transferring sensitive files, developers often provide a SHA256 hash alongside the file. After downloading the file, users can use a SHA256 hash generator to create the hash of the file and compare it with the provided hash. If the hashes match, the file is verified as unaltered.
This use of hashing SHA256 is critical in ensuring data has not been tampered with during transfer or download, which is especially important in software distribution and secure data handling.
3. Blockchain and Cryptography
SHA256 is the backbone of blockchain technology, including its most famous application in Bitcoin and other cryptocurrencies. In blockchain systems, SHA256 encryption is used to secure transaction data and ensure the integrity of the entire blockchain ledger. Each block in the blockchain is linked by a SHA256 hash, which guarantees that the data cannot be altered without breaking the chain.
By creating a unique, irreversible hash for every block, SHA256 helps maintain the trust and security of blockchain systems, preventing fraud and tampering. This makes it indispensable in the world of decentralized ledgers and cryptocurrency transactions.
The SHA256 Algorithm Explained
The SHA256 algorithm processes input data by breaking it into 512-bit chunks. Each chunk is processed through a series of bitwise operations, including shifting, rotating, and bit-mixing, to produce a final 256-bit hash. The result is a unique, fixed-length hash value that cannot be reversed or decrypted to reveal the original data.
SHA256 is a one-way hash function, meaning that once data is hashed, it’s practically impossible to retrieve the original input from the hash value. This makes it highly effective for tasks like password hashing and data integrity checks, where security is a top priority. The algorithm’s complexity and resistance to collision attacks have made it a trusted standard in modern encryption.
Why Use a SHA256 Hash Generator?
Our SHA256 hash generator is a versatile tool for anyone needing to create SHA256 hashes. It’s especially valuable for developers, IT professionals, and cryptography enthusiasts working on secure applications. Whether you’re hashing passwords, verifying files, or securing blockchain transactions, our online SHA256 generator provides a quick and easy solution.
Key Features:
- Fast and easy to use: No installation required; simply input your data and get your hash instantly.
- Secure and reliable: SHA256 remains one of the most secure hash functions available, widely used in encryption and data security.
- Online accessibility: Generate SHA256 hashes from any web-enabled device without the need for special software.
How to Use the SHA256 Hash Generator Online Tool?
Generating a SHA256 hash with our online SHA256 tool is simple and convenient. Here’s how it works:
-
Enter your data: Input the text, file, or data you want to hash into the tool’s input field.
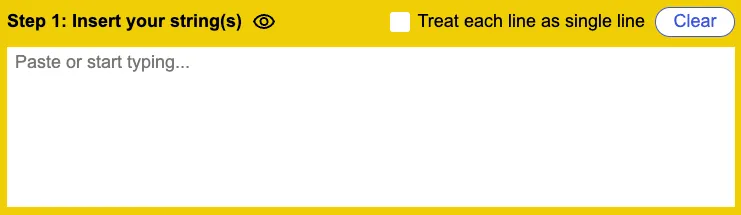
-
Click Generate: Hit the “Generate” button,

and the tool will produce a unique SHA256 hash of your data.
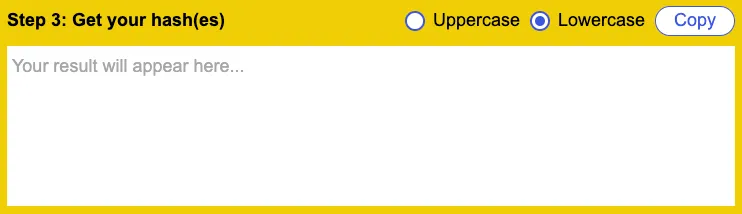
-
Copy the hash: Use the generated hash in your project, password storage, or data verification process.
The tool’s simplicity makes it accessible for users of all levels, and since it’s web-based, you can create SHA256 hashes from any device without additional software.
SHA256 Security Considerations
SHA256 is widely considered one of the most secure hash functions available today. Its 256-bit hash size and resistance to collision attacks make it suitable for encryption, password storage, and cryptography. Unlike older algorithms such as MD5 and SHA1, which are vulnerable to attacks, SHA256 offers strong security and remains trusted in many industries.
However, as with any security practice, it’s essential to stay updated with advancements in cryptography. While SHA256 is robust, stronger algorithms like SHA3 or new methods of encryption may emerge in the future. For now, SHA256 remains a top choice for secure hashing and encryption.
For more detailed information on modern cryptographic algorithms and secure practices, you can check out this article on cryptographic standards.
Conclusion
Our SHA256 hash generator online is a powerful tool for anyone needing to create secure hashes for password storage, file verification, or blockchain projects. SHA256’s strength and reliability have made it the gold standard in modern encryption, and our tool ensures you can quickly and efficiently generate SHA256 hashes anytime, anywhere.
Whether you’re working on a project that requires secure password hashing or ensuring the integrity of downloaded files, try our SHA256 hash generator and experience the simplicity of secure hashing at your fingertips.
