
How to Send Password Protected Email in Outlook? Complete Guide
Comprehensive step-by-step guide to Outlook email encryption with S/MIME certificates, Microsoft 365 encryption, and security best practices.
Read More

Comprehensive step-by-step guide to Outlook email encryption with S/MIME certificates, Microsoft 365 encryption, and security best practices.
Read More
Learn effective methods to password-protect Google Docs using Microsoft Word, Adobe PDF, extensions, and sharing controls for enhanced document security.
Read More
Comprehensive guide covering USB drive password protection through hardware encryption, software solutions, and security best practices for data safety.
Read More
Shield sensitive PDFs with critical layers, 4 setup steps, encryption tips & sharing safeguards. Learn smart ways to protect files from breaches.
Read More
Protect spreadsheets with 6 proven methods: link sharing, user roles, org rules, sheet locks, link expiry & 2FA. Keep sensitive data safe every time.
Read More
Learn how to lock Word files with steps, protection types, strong password rules, mistakes to avoid & key benefits for safer document sharing.
Read More
Master Excel file security with password protection methods, encryption techniques, and advanced security features. Protect sensitive data effectively.
Read More
Complete guide to PDF password protection. Learn Adobe Acrobat, online tools, desktop software, encryption standards, and security tips.
Read More
Master some proven methods to password-protect zip files with Windows, 7-Zip, and WinRAR. Learn AES-256 encryption and strong passwords to secure data.
Read More
Compare privacy, security, 2FA, mobile apps & password tools. See key differences in encryption, sync, interface, and account recovery to choose safely.
Read More
Check out 6 top Enpass alternatives with real-time sync, multi-factor security, breach alerts & family sharing. Upgrade password safety effortlessly today!
Read More
Compare 1Password's clean audits, 34-char Secret Key, & business tools vs LastPass's AES-256, 100,100 iterations, & key breach lessons before choosing.
Read More
See how length, character mix, attack methods, and hardware shape password survival, lasting seconds or centuries. Secure your data with smarter choices.
Read More
Understand password decoding techniques, learn how hackers crack passwords, and discover proven methods to create decode-resistant credentials for maximum security.
Read More
Learn proven methods to locate stored passwords using Windows Credential Manager, Command Prompt, browsers, and registry tools.
Read More
Master PC lock screen password changes with our comprehensive guide. Explore Settings app, Control Panel methods, and keyboard shortcuts for Windows 10/11.
Read More
Find the key basics, creation methods, OS setup steps, and advanced features to build unbreakable passwords that safeguard all your digital data.
Read More
Recover Gmail password on your phone in 4 ways: saved logins, phone verification, Google recovery, and future-proof tips with security checkups.
Read More
Stop automatic password leaks! Learn device methods, Chrome tricks, and Google account steps to secure credentials safely and stay in full control.
Read More
Create a user ID with 4 steps, rules, and 4 mistakes to avoid. Balance memory and safety like a health shield protecting your digital identity.
Read More
Shield your digital identity with 4 username tips, password rules, 5 account safeguards, and email security moves trusted by cybersecurity experts.
Read More
Discover predictable patterns, weak traits, and risky examples hackers exploit daily. Learn proven ways to stop breaches before they cost you thousands.
Read More
Unlock stronger security: big mistakes weaken 87% of passwords. Learn top symbols, smart placement tricks, and pitfalls to dodge for lasting safety.
Read More
Learn to create app-specific passwords with 4 setup steps, benefits, management methods, platform guides & fixes to solve 95% of login issues.
Read More
Discover the proven password practices, creation rules, attack types, and advanced defenses to protect your digital identity with stronger security.
Read More
Learn to create app-specific passwords with 4 setup steps, benefits, management methods, platform guides & fixes to solve 95% of login issues.
Read More
Learn your legal rights after data breaches. Discover compensation eligibility, required evidence, and protection strategies to safeguard your personal information.
Read More
Check if you can sue Facebook for data breaches, explore successful settlements, learn eligibility requirements, and find steps to protect yourself.
Read More
Explore how chip credit cards work against data breaches, their limitations, and essential security practices, including password management.
Read More
Stop costly breaches with layers of defense: strong passwords, multi-factor access, employee training, encryption, network checks, backups, and incident plans.
Read More
Explore the financial impact of Canva's massive 2019 data breach affecting 139 million users. Understand hidden costs, recovery expenses, and lessons learned.
Read More
Act in steps, fraud alerts, credit freezes, daily checks, FTC reports, strong passwords, 2FA, and safe storage to shield your SSN after a data breach.
Read More
Shield your business from breaches with these essentials: strong passwords, MFA, network safety, training, backups, encryption, and rapid incident response.
Read More
Uncover key privacy risks, consent rules, and safeguards to protect personal info when sharing emails. Stay compliant, avoid legal troubles now!
Read More
Essential data breach response strategies for finance companies. Immediate protocols, customer protection, compliance requirements, and security improvements.
Read More
Uncover if your info’s been leaked. Use key steps to create unbreakable passwords, enable 2FA, & block 15B+ threats now. Your digital health depends on it!
Read More
Prevent cyber threats with strategies: MFA, password policies, encryption, employee training, PAM, DLP tools, and strong cloud security measures.
Read More
Explore the true financial impact of data breaches in 2025, from average costs by industry to hidden expenses and long-term consequences affecting businesses globally.
Read More
Alarming 2025 data breach stats reveal daily cyberattack frequency, high-risk industries, costs, and detection times. Key cybersecurity insights you need to know.
Read More
Secure campus data with strong password rules, 3 network protections & encryption tactics to stop data breaches at Universities and protect student info.
Read More
Stop cyber threats with key steps like staff training, MFA, encryption, secure portals, device safety, vendor checks, and real-time network defense.
Read More
Shield your cloud with key tactics: strong authentication, encryption, access control, audits, threat detection, and monitoring to stop breaches fast.
Read More
Protect your smart gadgets with strong passwords, 2-step multifactor authentication, 3 network fixes, and browser tools to stop breaches before they start.
Read More
Reusing passwords can trigger 26B+ leaks, fuel 10B+ dark web trades & invites 3 types of attacks. Learn the ways to break the cycle before it's too late.
Read More
Protect your online identity using 12-character passwords, top tools, 5 best practices, and common mistakes to avoid. Stay safe across all devices today.
Read More
Explore credit freezes after a data breach, covering benefits, three-bureau steps, costs, limits, and ways to protect your financial identity.
Read More
Millions of weak passwords fuel dark web threats. From ID theft to fraud. Learn 3 real causes, 3 dangers & 4 ways to lock down your digital life now.
Read More
Explore the ways strong passwords shield your email from dark web threats, brute force attacks, reuse risks, and exposure through multi-layered security.
Read More
Guard your data from dark web hacks! Use proven methods: strong unique passwords, avoid reuse, check strength, detect phishing, and secure crypto wallets now.
Read More
Explore how dark web criminals target smartphones and learn key strategies to protect your device from cyber threats and malware.
Read More
Step-by-step instructions for updating your AOL email password on desktop and mobile devices, plus recovery tips and security best practices.
Read More
Essential Mac security tips for password management, email encryption, network safety, and system monitoring to prevent cyber threats and data breaches.
Read More
Step-by-step methods to reset your Mac password safely using Apple ID, Recovery Mode, and FileVault. Protect your data while regaining access to your Mac.
Read More
Hackers exploit 4 tactics, SIM swapping, SMS interception & more, to breach your phone-linked bank accounts. Act fast with 3 proven recovery steps now!
Read More
Our number can expose 3 threats: SIM swap, spoofing & more. Learn the ways to secure accounts, spot attacks, and protect sensitive health or ID data.
Read More
Learn 6 key warning signs like battery drain, heat, odd texts, high data use, and strange noises. Stay private with easy checks anyone can follow.
Read More
Explore essential strategies to secure your smartphone from hackers, including strong authentication, updates, app management, and privacy protection.
Read More
Essential guide to the most secure phones with insights on encryption, authentication, privacy controls, updates, and mobile threat protection.
Read More
Comprehensive Android phone protection strategies covering strong passwords, secure authentication, app safety, threat prevention, and ongoing security practices.
Read More
Essential cell phone security strategies to protect your digital life, avoid common mistakes, secure apps, strengthen passwords, and more.
Read More
Comprehensive guide to phone security apps, covering password generators, complexity testers, common mistakes, and Outlook app passwords for top protection.
Read More
Complete methods for transferring secure folders using Smart Switch, manual export, Samsung Cloud, and apps, plus security tips and troubleshooting.
Read More
Know the hidden risks of modified Telegram apps, including data theft and fraud, and learn key strategies to protect your privacy from cyber threats.
Read More
4 Key Reasons to enable two-step verification on Telegram and learn setup tips, threat prevention, and password best practices for stronger security.
Read More
Explore techniques to identify unauthorized access to your email and social media, plus tips on warning signs, password security, and quick response.
Read More
Essential strategies for recovering compromised social media accounts, boosting security, and preventing future breaches across all major platforms.
Read More
Explore essential security strategies to safeguard your PayPal account from cyber threats and reduce risks through strong passwords, 2FA, and phishing awareness.
Read More
Protect yourself when your phone number is compromised with expert tips on securing accounts and preventing identity theft. Learn recovery and prevention steps.
Read More
Explore the dangerous consequences of password reuse, from hacks to identity theft. Know how hackers exploit reused passwords and discover security strategies.
Read More
Explore how to spot a phishing scam before it steals your password. Understand red flags, technical signs, and security measures to protect accounts.
Read More
One password breach can cause devastating impacts like identity theft and financial loss. Learn proven strategies to secure your digital life now.
Read More
Know the proven ways to recover a hacked Crunchyroll account, boost email and device security, avoid password reuse, and stay safe with 2FA & audits.
Read More
Twitter account hacked? Learn the key steps to recover access, secure passwords, remove threats, enable 2FA & prevent future attacks. Stay protected now.
Read More
Complete guide to recover hacked Spotify accounts with step-by-step recovery process, security implementation, prevention strategies, and FAQs for protection.
Read More
Find out how to recover your hacked LinkedIn account and prevent future breaches. Discover password security tips, 2FA setup, and more protection strategies.
Read More
Explore how to recover hacked Amazon accounts, prevent fraudulent orders, and protect your financial information. Complete guide with recovery steps.
Read More
Starbucks Account Is Hacked? Discover 5 essential actions, reasons why breaches happen, and how to protect your account from future attacks effectively.
Read More
Explore how to regain control of your hacked Gmail by following 5 simple steps. Get tips on strengthening your security to prevent future hacks.
Read More
Instagram account hacked, phone number changed? Follow 5 urgent steps to recover access, verify identity, boost security and avoid future hacks. Act fast.
Read More
TikTok account hacked and email changed? Explore 5 proven ways to recover access, secure your profile, avoid scams, and stay protected from future attacks.
Read More
Knowing the risks of email hacking without a password can help protect your information. Discover how vulnerabilities can be exploited and what you can do.
Read More
Google account hacked? Follow these 5 urgent steps: recover access, secure settings, scan for malware, alert contacts, and stop future hacks fast.
Read More
My Facebook was hacked and password changed? Use these 7 essential steps, from recovery tools to 2FA, to regain control and lock down your accounts fast.
Read More
Can someone hack my passwords from Chrome storage? Find the risks, safer alternatives, expert tips, and why 2FA & password managers matter more than ever.
Read More
Explore 3 ways hackers detect password changes, from keyloggers to recovery access. Learn 7 actions to protect your accounts and stay safe online.
Read More
Explore 7 essential steps to build a strong cybersecurity routine, protect valuable assets, and foster a security-aware culture to combat digital threats.
Read More
Many wonder if biometrics or strong passwords offer better security; discover which method truly stands as the ultimate defense against unauthorized access.
Read More
Explore 7 essential security practices for e-commerce stores to protect your business, secure customer data, and stay ahead of evolving cyber threats.
Read More
Check out how to create strong passwords for cloud storage with tips on length, complexity, uniqueness, management tools, and password safety best practices.
Read More
Protect your child's digital world with essential knowledge every parent should know to secure kids' online accounts and ensure a safer internet experience.
Read More
Understand the hidden dangers of reused passwords and the best practices to protect your online security from breaches and unauthorized access.
Read More
Protect your crypto! Learn how to create uncrackable passwords with symbols, 2FA, and secure storage. Don't risk your assets, fortify your wallet now!
Read More
Boost your app's security with a strong password generator API, customizable, encrypted, and user-friendly. Arm users with unbreakable digital shields!
Read More
Are browser password generators truly safe? Discover their pros, hidden risks, and why dedicated tools may be your best bet for securing sensitive data.
Read More
Protect your accounts from hackers! Learn why strong passwords are essential for social media, banking, and more. Safeguard your data with expert tips!
Read More
Protect your data from AI hackers! Use strong password generators, MFA, VPNs & updates to outsmart cyber threats. Learn how to boost your defenses now!
Read More
Boost security, cut breaches, and boost productivity! Discover why every business needs a strong password generator to stay safe and compliant now!
Read More
Stop hackers in their tracks! Discover 5 powerful ways to prevent password reuse with MFA, SSO & password managers. Protect your accounts now!
Read More
Protect your small business from cyber threats! Discover top password managers with dark web monitoring, team controls & ISO-certified security.
Read More
Lock down your digital vault! Discover how to secure your password manager with 2FA, strong passwords, zero-knowledge tech & expert tips in this guide.
Read More
Boost security & slash IT workload! Discover how a centralized password manager stops breaches, speeds logins & ends password fatigue, instantly.
Read More
Boost your online security with 2FA! Protect against hacks, phishing & weak passwords. Learn how this simple step shields your sensitive data.
Read More
Unlock unbreachable security! Master passwords, 2FA, & anti-phishing tips inside. Don't risk hacks! Learn expert password manager strategies now!
Read More
Explore the top 5 factors to consider when choosing the most secure password manager and some of the best options to protect your sensitive data effectively.
Read More
Recognize common mistakes when creating and using passwords. Explore tips to strengthen security, avoid vulnerabilities, and safeguard your accounts.
Read More
Unlock ultimate security: Master robust policies, tech safeguards, secret password tips & employee training to defy cyber threats. Act now!
Read More
Transform your Google Drive into a digital fortress! Secure your Android with 2-step verification, encryption & more. Click now for ultimate protection!
Read More
Learn how to securely send credit card info via email with encryption, password protection, and secure services. Protect your financial data today!
Read More
Follow 5 simple steps to reset your Gmail password without security questions and explore tips to successfully recover your account and enhance its security.
Read More
Check out the security features and limitations of Google Password Manager and decide if it's the right choice for your password management and security needs.
Read More
Understand how often to change your passwords for maximum security. Learn key situations, password-strengthening tips, and best practices to stay protected.
Read More
Explore effective techniques for creating secure passwords using memorable and complex passphrases and protect your online security.
Read More
Why does Windows Security keep asking for a username and password? Discover the hidden causes behind this frustrating issue and how to resolve it.
Read More
Get ready to discover four effective methods to print a secured PDF without a password, from using password removal tools to converting files for easy printing.
Read More
Find out how to generate a Gmail app password in 7 simple steps for secure access from third-party apps without compromising your main password.
Read More
Explore how to generate an app password for Outlook with these 5 simple steps. Secure your Microsoft account and ensure a hassle-free connection today.
Read More
Get to know the security of Excel passwords, encryption strengths, and best practices to safeguard your sensitive data from unauthorized access.
Read More
Explore 4 effective ways to create strong, memorable passwords from words to enhance your online security and protect your accounts.
Read More
Check out the factors that determine the safety of online password generators and how to securely create and store passwords for enhanced online security.
Read More
Secure your Notion website with password protection! Learn 3 easy ways to lock your content using third-party tools & strong passwords.
Read More
Secure your Mac folders with encryption! Learn how to password-protect folders using Disk Utility or Terminal & keep your data safe from prying eyes.
Read More
Unlock password-protected Word files easily! Follow key steps for Word 2010 & earlier. Remove restrictions & regain access fast. Click to learn how!
Read More
Unlock & merge password-protected PDFs easily! Learn to remove passwords & combine files using Adobe, online tools & free software. Click to simplify!
Read More
Secure your Remote Desktop now! Follow these simple steps to change your password, boost security, and protect your data from potential threats.
Read More
Secure your Linux system! Learn how to change your root password, prevent breaches, and protect sensitive data with strong passwords.
Read More
Protect patient data & stay HIPAA-compliant! Learn why updating EHR passwords and using 2FA & password managers is key to stopping cyber threats.
Read More
Discover the top practical uses of a 4-digit random generator to enhance your security and streamline everyday tasks, from PIN codes to temporary passwords.
Read More
Secure your accounts with a 6-digit password generator! Learn how it enhances unpredictability, thwarts hackers, and boosts multi-layered protection.
Read More
Check out how to generate a strong password online with a secure alphanumeric characters password generator to boost security and protect information.
Read More
Check out how to create strong random passwords to protect your online accounts. Follow our step-by-step guide for enhanced security and password management.
Read More
Boost your online security with a free random password generator! Create strong, unique passwords effortlessly & avoid data breaches. Try it now!
Read More
Boost security with humor! Discover how funny password generators create memorable, strong passwords that are engaging & easy to recall. Try now!
Read More
Secure your Wi-Fi with strong passwords! Use a generator, mix characters, avoid predictability, update regularly & fortify your network!
Read More
You might underestimate the importance of random password generators, but they could be your best defense against growing cyber threats. Discover why they're essential.
Read More
Learn how to craft a secure password with 12+ characters using symbols, numbers, and letters. Avoid hacks with tips on MFA, encryption, and password managers!
Read More
Learn how to use Chrome to generate strong passwords on iPhone. Enable Google Password Manager, sync devices, & enhance online security with this simple guide!
Read More
Think strong passwords keep you safe? Discover why MFA, password managers, random generators, and vigilance are essential for securing your accounts from hackers.
Read More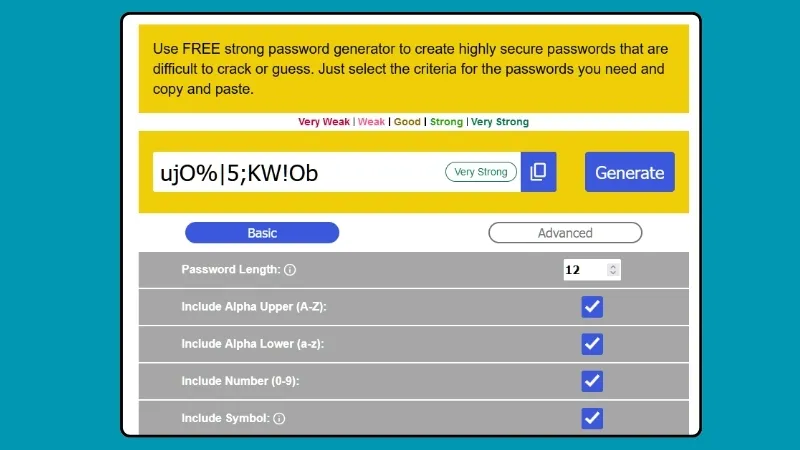
Boost online security with encrypted password generators. Learn how they create strong & unique passwords to prevent hacks and streamline your safety.
Read More
Learn how to generate strong, unique passwords & manage them securely. Protect your data with tips on randomization, passphrases, and password managers.
Read More
Discover how a strong password can protect your privacy! Learn secrets for creating complex, unique passwords to prevent data breaches and identity theft.
Read More
Learn about the risk assessment of common ATM pins and their potential measure to secure your financial instrument and keep yourself safe from theft.
Read More
Explore the challenges of password management in a digital age. Uncover reasons behind public aversion and discover solutions for a secure online future.
Read More
Dropbox and two-step verification; learn how to set it up and enhance Dropbox security to secure your files and data with an extra layer of protection.
Read More
Explore the potential risks of using smartphones for work. Navigate the risks of this habit wisely for a balanced and efficient professional experience.
Read More
Explore the alarming state of cybersecurity in our digital age. Uncover threats, vulnerabilities, and proactive solutions. Stay informed, stay secure.
Read More
Check our QuickLock review and unlock the truth about this app. Discover its features, security, and user experience, and know what you are buying.
Read More
Explore the pervasive threat of cybercrime on individuals and businesses. Uncover the risks, protective measures, and real-world impact in this analysis.
Read More
Learn how this modern world is changing the future of passwords as more complicated methods are surfing to crack the user's best online defense.
Read More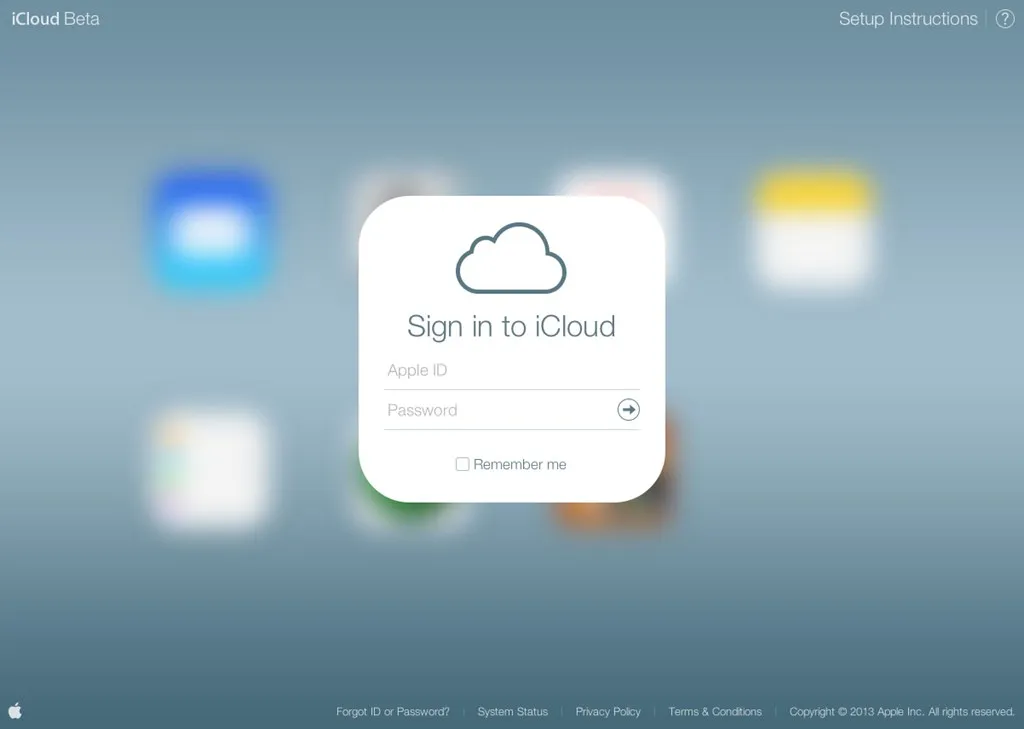
Unlock seamless security with our guide on how to use Apple's iCloud Keychain and secure passwords effortlessly on all your devices from one account.
Read More
Learn essential tips on avoiding phishing emails. Secure your digital identity with expert advice and stay one step ahead of cybercriminals.
Read More
Explore customer protection measures for secure online shopping. Safeguard your transactions in e-commerce with advanced security practices.
Read More
Craft the best defense strategy with our Business Cyber Security Plan. Safeguard your enterprise from digital threats effectively.
Read More
Protect your website from SEO poisoning with robust domain security measures. Learn how to safeguard your online presence and enhance SEO resilience.
Read More
Unveil the truth behind common file transfer misconceptions! Explore efficient data exchange strategies and debunk myths for seamless file-sharing success.
Read More
Learn data erasure with File Shredder – the ultimate tool to delete files and protect sensitive information safely. Delete your data the right way for peace of mind.
Read More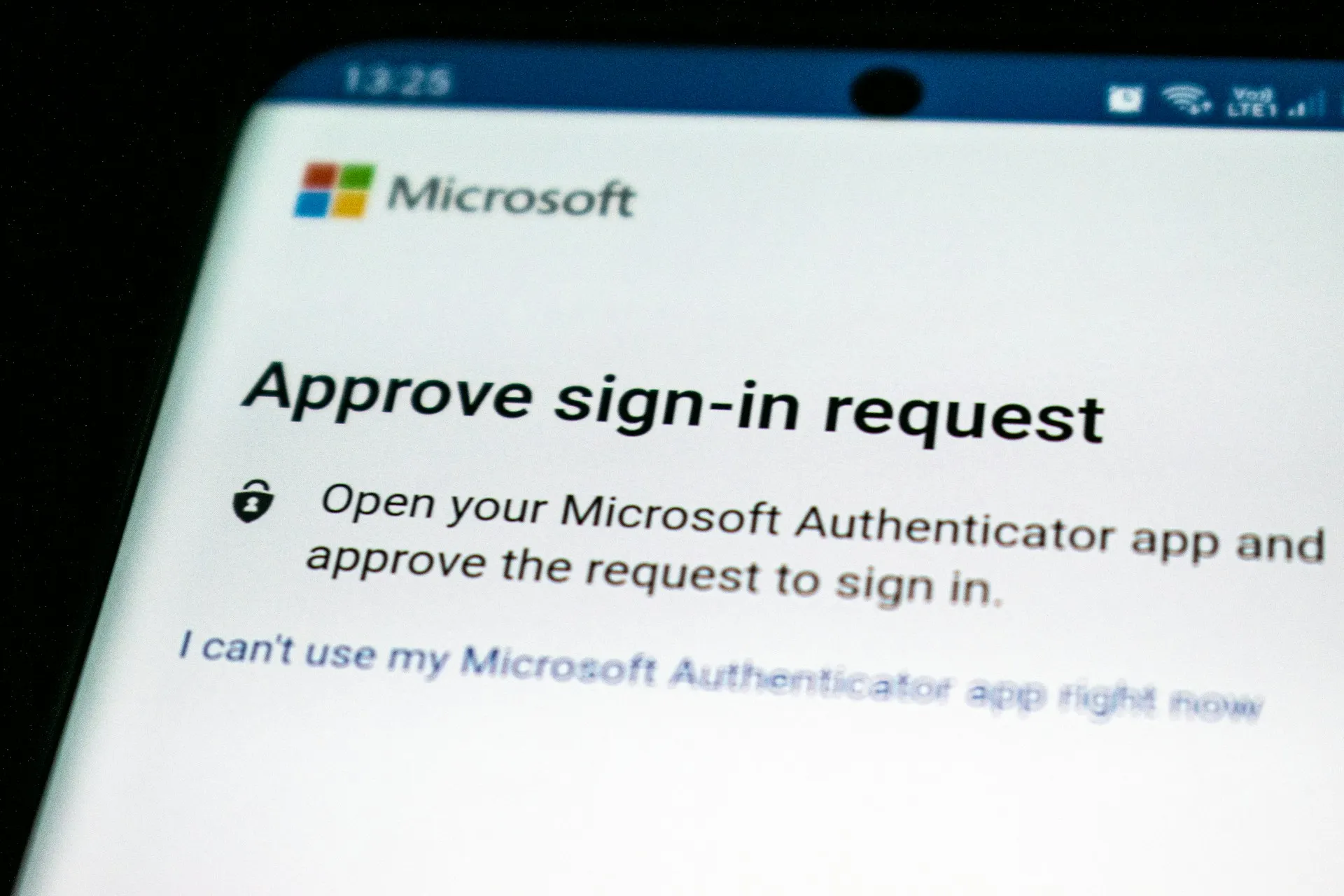
Discover the nuances between Anti-Virus and Anti-Malware tools. Uncover the best options to fortify your digital defenses. Keep your system safe.
Read More
Enhance your digital identity! Discover the best strategies and tools to safeguard your computer against hackers. Stay ahead in cybersecurity.
Read More
Discover top internet security practices in this guide. Protect your digital identity with expert secrets for online protection and avoid future threats.
Read More
Protect your Mac from MacDefender Trojans! Learn effective removal techniques, secure your system against future threats, and secure your digital world.
Read More
Enhance corporate security with expert insights on corporate data leakage and spy monitoring. Discover robust strategies to safeguard sensitive information.
Read More
Is your password truly protecting you from online attacks? Discover the truth about its strength and uncover essential tips for your online security.
Read More
Discover the best password strategy for foolproof data security! Uncover the only solution you need to safeguard your information effectively.
Read More
Learn about the 25 worst passwords of 2025 and avoid using them to secure your accounts because they are easy for hackers to crack and steal your data.
Read More